How does .locky file extension virus spread and how does it act?
There are many ways how .locky file extension virus can enter your computer system. Remember that cyber criminals use clickjacking techniques to deceive naive computer users and force them to click on malicious links that are disguised as safe-looking ones. In other words, cyber criminals might conceal .locky file extension virus download link under a button or a link that looks completely safe on untrustworthy download websites. Be a security-minded computer user and bypass visiting websites that cause even a slightest suspicion of a trap.
However, cyber criminals mostly distribute .locky file extension virus via fraudulent emails that include a malicious attachment (Word document). This Word file includes a code that gets activated immediately in case the user has Macros function enabled in Word. In case Macros is disabled, the user sees a message above a distorted text: “Enable macro if the data encoding is incorrect.”

As we have mentioned above, Macros activates the code, which is designed to download and run an executable .locky file extension virus file from a remote server. This disastrous program then scans the computer system, detects victim’s personal files and encrypts them using RSA-2048 and AES-128 encryption methods. There is a reason why Locky is referred to as .locky file extension virus - once this threat encrypts personal files, it also adds a .locky extension to the filenames. Encrypted data becomes inaccessible; in such way, this virus puts the victim in an invidious position. Obviously, every computer user keeps important data on its computer, so such deprivation of files can cause desperation and stress. However, .locky file extension virus leaves ransom notes in every folder that holds the encrypted data, and this note explains how the victim can retrieve his/her personal records. .locky file extension virus asks to pay a ransom (0.5 Bitcoin, which is equal to 207 US dollars).
It is advisable not to pay the ransom. No matter how much you pay, cyber criminals only care to make a profit. There is absolutely NO guarantee that they will send you decryption key to recover your personal files. Do not support cyber criminals this way. Otherwise, you take a risk losing your files AND your money. Besides, cyber criminals will know that they can scare you and might try to send another virus for you in the future.
How to protect your computer from ransomware?
- The most important thing to do is to regularly backup your data. We recommend you to store copies of important data on an external drive because some ransomware viruses can access online file storage clouds via your Internet connection.
- Install a reputable anti-malware software (for instance, SpyHunter) on your computer to keep it protected from ransomware and other dangerous viruses.
- Whenever you download files or programs, choose “Save” option instead of “Run/Open.” This way, you give some time for computer security software to check whether the file is safe or not.
- Keep all your software up-to-date - enable automatic software updates if possible. Cyber-criminals can exploit vulnerabilities in outdated software and enter your system without your knowledge.
- Avoid visiting high-risk websites and download software only from verified and secure download websites.
How to decrypt files locked by .locky file extension virus?
Unfortunately, it is nearly impossible to decrypt files that were encrypted by this malicious computer threat. The only one way to recover your files is to import them from an external drive. If you did not create any data backups earlier, then you can try one of the following tools to decrypt your files - Photorec, Kaspersky virus-fighting utilities or R-Studio.
It is important to kill .locky file extension malware as soon as you notice its presence. If you notice its existence soon enough, you might be able to stop the encryption process in time and save some of your files. If you plan to import data from the external backup drive, make sure you entirely remove .locky file extension virus first, as this threat is capable of accessing and encrypting data on every device plugged into the computer as well. We strongly recommend using an automatic malware removal tool to terminate Locky virus; however, if you wish to do it manually, please follow Locky virus removal instructions that are provided below this article.
.locky file extension virus FAQ:
Question: Today, I have received a suspicious email. The subject is: ATTN: Invoice J-98223100. This email also has a file attached to it, which is named invoice_J-98223100.doc. I believe that this email is untrustworthy and that I shouldn’t open it… However, how can a Word file be dangerous? Can you explain what should I do about this email? Should I open the attachment or should I send this email to Trash?
Answer: Do NOT open the attachment! You have received an email from cyber-criminals related to Locky ransomware. This fraudulent email delivers infectious Word document that can download a virus to your computer.
Locky virus uses a new technique to download and run virus executable file - it sends a malicious code in a Word document, which gets activated if Word Macros function is toggled on. You should send this email to Trash immediately.
By downloading any of provided Anti-spyware software you agree with our Privacy Policy and Agreement of Use.
Happiness
Guarantee

Method 1. Remove .locky file extension using Safe Mode with Networking
- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see theAdvanced Boot Options window.
- Select Safe Mode with Networking from the list

- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
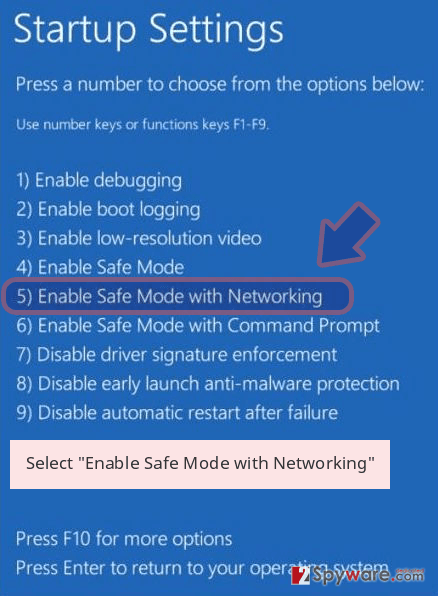
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
- Once your computer becomes active, select Enable Safe Mode with Networking in Startup Settings window.
Log in to your infected account and start the browser. Download SpyHunter or other legitimate anti-spyware program. Update it before a full system scan and remove malicious files that belong to your ransomware and complete .locky file extension removal.
If your ransomware is blocking Safe Mode with Networking, try further method.
Method 2. Remove .locky file extension using System Restore
- Click Start → Shutdown → Restart → OK.
- When your computer becomes active, start pressing F8 multiple times until you see theAdvanced Boot Options window.
- Select Command Prompt from the list

- Press the Power button at the Windows login screen. Now press and hold Shift, which is on your keyboard, and click Restart..
- Now select Troubleshoot → Advanced options → Startup Settings and finally press Restart.
- Once your computer becomes active, select Enable Safe Mode with Command Prompt in Startup Settings window.

-
Once the Command Prompt window shows up, enter cd restore and click Enter.

-
Now type rstrui.exe and press Enter again..

-
When a new window shows up, click Next and select your restore point that is prior the infiltration of .locky file extension. After doing that, click Next.


-
Now click Yes to start system restore.

After restoring your system, you should remove all malicious files that belong to .locky file extensionbecause they are still on your computer. For that, download SpyHunter and scan your PC.
If you have individual files to decrypt, now it’s time to use Windows Previous Versions feature. For that, select a file, right click on it and select Properties. Now go to Previous Versions tab and look for a restore point of your file. Select it if it’s there and click Restore. Beware! This method is effective only after enabling the System Restore function. Besides, if your ransomware is designed to removeShadow Volume Copies of the files, it may fail to work for you. In this case, try Photorec or R-studio..
If this free removal guide helped you and you are satisfied with our service, please consider making a donation to keep this service alive. Even a smallest amount will be appreciated.
Chia sẻ & Hỗ trợ
- có nên Defragment ổ đĩa SSD không?
- 5 thói quen khiến máy tính Windows chạy chậm
- STEP by STEP to Select Multiple Messages Quickly in Gmail, any email
- How to FIX YouTube Embed AUTOPLAY not working
- iPhone's AI works fastest ✔ Biến iPhone thành AI làm việc SIÊU TỐC
- How to make EASY Money Online
- So sánh Windows 10 Home vs Windows 10 Professional
- HOW To Fix SSL Errors | This certificate has expired or is not yet valid
- POP and IMAP email settings for Outlook
- Bàn phím thông minh cho Windows 10













